Below are my responses associated with the Cyber Security & Awareness – Primary Years (2021) MOOC. As is my way with MOOCs, I have dipped in and out of the course when time allowed.
Unit 2 – Computer Science Fundamentals
Explain what you think are some of the key differences between cyber security, cyber awareness and cyber safety. To what extent are you teaching these in the classroom or to what extend do you think they should be taught and why?
For me, Cyber Security is about the solutions and services that keep us protected. This might involve people and programs. It can be understood as being a part of what Ursula Franklin described as technology as a system:
Technology is not the sum of the artefacts, of the wheels and gears, of the rails and electronic transmitters. Technology is a system. It entails far more than its individual material components. Technology involves organization, procedures, symbols, new words, equations, and, most of all, a mindset.
Cyber Awareness on the other hand is having some knowledge and understanding of this system and how it fits together, while Cyber Safety is the action of this knowledge and understanding.
One way of appreciating this divide is to divide the topic between mindset and skillset. This is something that Doug Belshaw touches upon in his exploration of digital literacies.

For example, consider an application like Hapara. From the perspective of mindset and understanding:
- Cognitively and confidence involves appreciating new ways of working. Although it may be more efficient, if you have been using GSuite, these are still habits to unlearn and relearn.
- From a critical and civic point of view, it is important to consider why there is a need to manage learning at all and the consequences associated with such actions.
Whereas from the perspective of skillset and actions:
- From a cultural perspective, Hapara posits that teachers are largely responsible for creating the conditions for learning.
- Constructively, there is a blur between empowering students with the power to participate in actions and the dangers in excessively moderating their learning.
- From a communicative point of view, GSuite allows a number of ways to engage, Hapara provides the means to manage and moderate this within different cultural norms.
- Connecting with GSuite through the use of APIs, Hapara has the ability to both hinder and help the creative process depending on how it is deployed.
I have elaborated this more here.
Share with the community a way you would like to introduce networks into the classroom to make it tangible or visible for primary students. It could be using a resource you have found or your own idea or thoughts.
Two activities that I have used in regards to helping student appreciate networks are paper blogs and mapping the internet.
PAPER BLOGS
Students use the a template to create a paper blog post. They then post it on the World Wide Whiteboard.
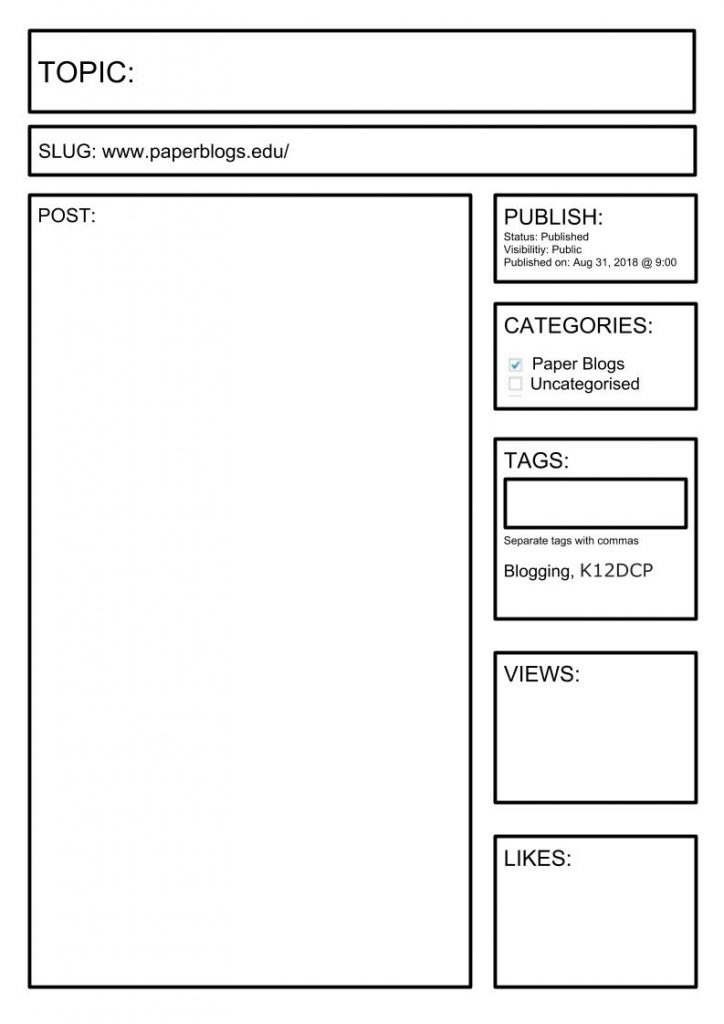
Students then walk around the room and read the posts leaving various data traces, such as:
- Tick to mark they had read the post.
- Star if they liked the post.
- Sticky Note with a comment
This was adapted from the work of Bianca Hewes.
MAPPING THE INTERNET
In response to Marc Prensky published two articles in 2001 in which he coined the terms digital native and digital immigrant, David White and Alison Le Cornu offer a more fluid typology with their notion of digital visitor and resident.
When in Visitor mode, individuals decide on the task they wish to undertake. For example, discovering a particular piece of information online, completing the task and then going offline or moving on to another task.
Where as:
When in Resident mode the individual is going online to connect to, or to be with, other people. This mode is about social presence.
Students are given a copy of the the map of the internet and are asked to plot the various spaces they exist in online and where they sit along the continuum.

This is activity is useful for thinking about the networks they are a part of and the way in which their data is spread across the web.
Thinking about this activity now, it is interesting to consider this in regards to cyber awareness and what data we share even when we are just ‘visiting’.
Share an activity idea or classroom resource that you have found online or created yourself that involves primary students exploring private and public information sharing. It could be a video, lesson plan, storybook, song or anything else!
One resource that I have found really useful in exploring the divide between public and private sharing has been blogs using Global2/Edublogs. Students created blogs focusing on a passion. The sites were viewable by other students in the class, but not anybody outside of that. These were all connected by a classroom blog, which was made public. This served as a resource as well as a example. For me, the interconnected nature of these sites allowed students to interact through the Dashboard Reader, helping create something akin to a social media space. Blogs served as a tool to learn with in that students were able to share their ideas and learnings, as well as learn about sharing information, both private and public, and how we interact with this information.
Unit 3 – Information Safety and Security
We have shared a few examples of how information can be extracted from data (such as in your images). What are other ways humans can leave traces of information with the use of technologies? Share an example or examples with the community.
Some other examples of where information can be extracted from data include:
- Test scores, learning artifacts and plagarism software used to make judgement using machine learning.
- Information surreptitiously shared when using various apps on a smartphone. Even de-identified data can leave a trace.
- Facial recognition taken from CCT cameras, so of which are open and public.
- Wearables and the plotting of location data, including secret US Army bases.
- Genetics tests potentially used to identify supposed taste in music or links to a crime.
What other interesting examples of codes from history or the modern-day (digital or non-digital) can you find to inspire or support a lesson about encoding and decoding messages?
For those wanting to go to the next level in regards to encryption could look at the Enigma Machine from World War II.
This coding machine used by the Germans in World War II involved a two step process. Firstly, the machine itself had a keyboard which once pressed ran a signal through a number of variables, including rotors and plugs, which helped to scramble the code. This all depended on a second documented which stipulated how the rotors and plugs were to be set. So in order to break the code you would need both the machine and the current configuration. In some ways this has similarities with private and public encryption, where somebody maybe able to get access to the ‘public’ machine, but unable to make any sense of this without cracking the ‘private’ configuration.
Paul Scruton has visualised how the Enigma Machine worked in this Guardian infographic:

While Tom MacWright has created a virtual model of the machine which allows the user to not only configure the machine and enter a message to be encrypted, but also follow the signal as it passes through the various stages.
Find and share a resource to support teaching students in primary years about information sharing or safe communication. Include a brief description.
COMMENTING ON BLOGS
When introducing blogging in the classroom, I used to follow up my focus on paper blogs with a focus on commenting and communication. This began with a ‘turn and talk’ about why we communicate online? I would then watch Linda Yollis’ video on quality comments.
After watching this, students worked together to complete a Found Out, Made Me Think.
Once the class had thought about comments, we created a set of guidelines which were then used in the creation of a rubric that students could be used as a reference. To support this students refereed to the Rubric for Rubrics to help them.
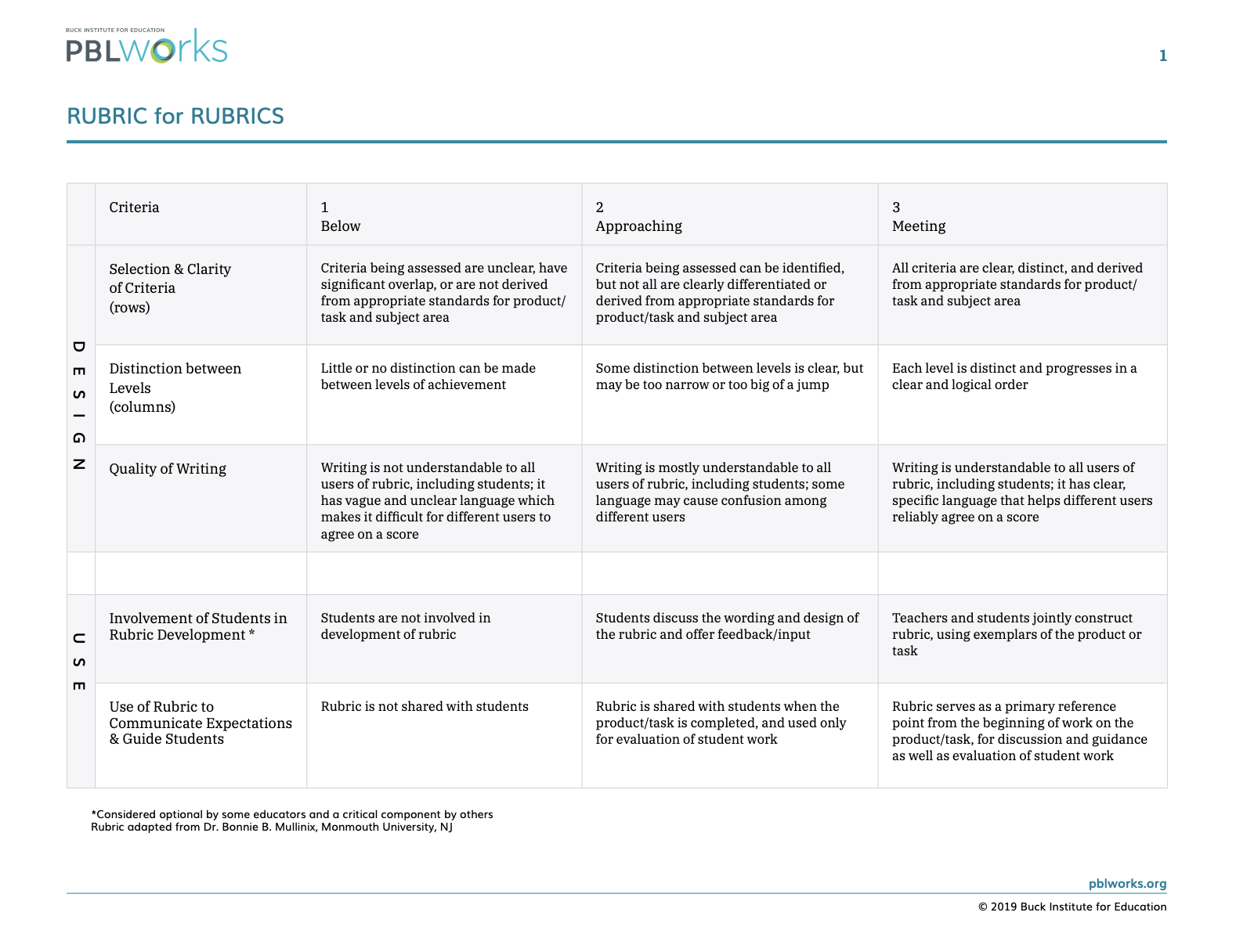
What mattered most for me was creating a space where students could learning through the experience of commenting, especially as some of my older boys were already engaging in 4Chan, meme and trolling culture. Therefore, this rubric was something that we returned to regularly as particular situations arose.
Thinking about this now in regards to the challenges of moderation on social media (see posts about YouTube and Facebook), I wonder about extending this by discussing what changes they would make if they were moderating comments for every class in the school (or even whole world) and what a digital solution for this might look like?
Unit 4 – Internet Security
What are some primary-friendly “scam scenarios” that you could use in the classroom for encouraging students to critically think about messages they receive? Create your own “fake scam” to share with the community so they can try and spot the tell-tale signs!
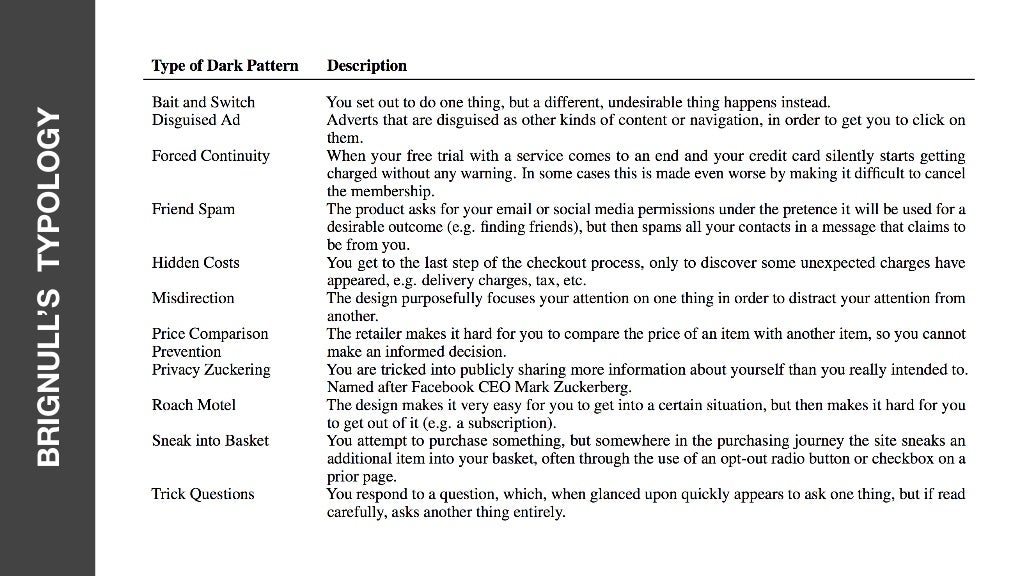
Rather than Nigerian prince or stranger danger, I think that the best scam that children need to learn to be aware of are the surreptitious scams they learn to live with every day. These are what Harry Brignull coined as ‘dark patterns‘.
Dark Patterns are intentional user interfaces to trick you into doing something. As Brignull explains:
Normally we think of bad design as consisting of laziness, mistakes, or school-boy errors. We refer to these sorts of design patterns as Antipatterns. However, there’s another kind of bad design pattern, one that’s been crafted with great attention to detail, and a solid understanding of human psychology, to trick users into do things they wouldn’t otherwise have done. This is the dark side of design, and since these kind of design patterns don’t have a name, I’m proposing we start calling them Dark Patterns.
In an interview with Brignull, Per Axbom and James Royal-Lawson provide their own definition of dark patterns as,
A gap between perception of what you are doing and the reality of what you have done. – 30 mins
While in Mike Monteiro’s book Ruined by Design, he argues that:
Dark patterns are the canaries in the coal mine of unethical design. A company who’s willing to keep a customer hostage is willing to do worse.
Arvind Narayanan, Arunesh Mathur, Marshini Chetty, and Mihir Kshirsagar suggest that such patterns have developed over over over time:
Although they have recently burst into mainstream awareness, dark patterns are the result of three decades- long trends: one from the world of retail (deceptive practices), one from research and public policy (nudging), and the third from the design community (growth hacking).
Harry Brignull has created a site dedicated to all things dark patterns, including a list of examples:
- Trick questions while filling in a form
- Sneak into the purchase basket
- Roach motel
- Privacy sharing
- Price comparison prevention
- Misdirection and distraction
- Hidden costs
- Bait and switch
- Guilting users into opting into something
- Disguised ads
- Forced continuity
- Friend spam
Colin Gray summarises these in a presentation on the dark side of UX design:
Alternatively, the research team at UXP2 have broken Brignull’s list down into five particular strategies:
- Nagging
- Obstruction
- Sneaking
- Interface Interference
- Forced Action
In the end, Daniel Fitton suggests that what is most important is a critical understanding.
Dark design is used to influence our decisions about our time, our money, our personal data and our consent. But a critical understanding of how dark patterns work, and what they’re hoping to achieve, can help us detect and overcome their trickery.
The question is what this all means for young children. When you scroll through the abundance of examples shared in the subreddit community and in Brignull’s hall of shame, they seem beyond the world of a twelve year old, let alone a five year old. However, it could be argued that so many habits actually stem from what actually happens during the early years and how technology is approached. Thinking about this from the perspective of digital literacies, so much time is spent on skillsets, such as being creative and communicative, but mindsets, such as critical and cognitive thinking, are just as important.

Therefore, thinking about patterns in general, the focus at at F to 2 could be to explore the shapes and colours used in applications. Investigate the ways we represent information about applications using software and digital systems. Use software to create a positive and a negative representation of data. Investigate in-app purchases and the ways users are enticed to sign-up or purchase add-ons for additional features, like stickers and bonuses.
In 3 to 4, students might explore the different types of data engaged with in online spaces. This could include something like paper blogs and leaving physical dots to represent engagement. As well as continue to explore the representation of different types of data and information, including the application of ethical and social protocols.
In 5 to 6, students could form a definition of dark patterns and how they impact users. This could include the developing solutions which demonstrate such patterns. Associated with this, they might develop protocols for how to respond to such patterns.
FURTHER RESOURCES
Create or find a classroom resource that teaches students about creating strong passwords, passcodes or passphrases.
— #Leunig Cartoons (@leunigcartoons) July 20, 2019
There is so much written about passwords, what makes a strong ones, how to go about maintaining them. For example, the Twinkl team recommends six rules:
- include numbers, letters and symbols
- use at least one capital letter
- make it something you will remember but others won’t think of
- make sure it has eight characters or more
- never use obvious names or dates
- never write down or share your password
While Charlotte Empey’s provides the following tips:
- Stay away from the obvious
- Make it long
- Use a mix of characters
- Avoid common substitutions
- Don’t use memorable keyboard paths
- Avoid using single words
Associated with these tips, she puts forward some particular strategies:
- Revised passphrase method where you compose a phrase using bizarre and uncommon words a phrase that gives you a mental image.
- The sentence method combines a random sentence with a rule that makes it gobbledegook.
- Muscle memory method where a random group of characters is memorised as a pattern.
Micah Lee elaborates on the discussion of passphrases, discussing the Diceware method:
First, grab a copy of the Diceware word list, which contains 7,776 English words — 37 pages for those of you printing at home. You’ll notice that next to each word is a five-digit number, with each digit between 1 and 6. Here’s a small excerpt from the word list:
24456 eo 24461 ep 24462 epa 24463 epic 24464 epochNow grab some six-sided dice (yes, actual real physical dice) and roll them several times, writing down the numbers that you get. You’ll need a total of five dice rolls to come up with the first word in your passphrase. What you’re doing here is generating entropy, extracting true randomness from nature and turning it into numbers.
If you roll the number two, then four, then four again, then six, then three, and then look up in the Diceware word list 24463, you’ll see the word “epic.” That will be the first word in your passphrase. Now repeat. You want to come up with a seven-word passphrase if you’re worried about the NSA or Chinese spies someday trying to guess it (more on the logic behind this number below).
Using Diceware, you end up with passphrases that look like “cap liz donna demon self,” “bang vivo thread duct knob train,” and “brig alert rope welsh foss rang orb.” If you want a stronger passphrase you can use more words; if a weaker passphrase is OK for your purpose you can use less words.
In Richard Barnes’ guide to safer logins, he suggests
- Use random passwords, and use a different password for every site
- Use a password manager to make creating and remembering passwords easier
- Make your answers to security questions just as strong as your passwords
- Use “two-factor authentication” wherever you can
- Pay attention to the browser’s security signals, and be suspicious
Elaborating on two factor authentication, Chris Betcher explains it as ‘something you have and something you know‘:
The something you know is the password, and yes it’s still a good idea to have a strong password, something with enough length and complexity that is hard to guess but easy to remember. But it’s not enough. It’s just one factor.
The second factor is something you have, or something you physically carry with you, such as a phone or touch key. Unless the hacker or foreign power actually has your phone, they can’t access your data, even if they know your password. Just like the two keys for the front door, they need both your password AND your phone at the same time. If they have both those things, you may just have bigger problems to deal with.
All this advice is helpful, but not necessarily practical for young learners. Although a passphrase made using the Diceware method used in association with two-factor authentication may be considered an ideal outcome, the question remains how young learners are supported with building up their confidence and constructive capacity to manage such workflows?
In regards to learning activities, there are various resources available, however too often they come across as one-off lessons, a passing of the knowledge akin to the Matrix, rather than a gradual release over time.
The risk with this approach is that if a student was not there for this one-off experience, then they can miss the transer of knowledge.
One person to approach the problem differently is Audrey Nay, she has put together a continuum of learning starting at Prep and going to Year 6. The journey starts with a basic passwords letters and ending with a 6 character mnenomic with a mixture of numbers, upper and lower cases, and punctuation. Although I like how she has broken down the sequence of steps across the years, I wonder about the outcome of a 6 character mnenomic, as opposed to a passphrase. As Micah Lee explains:
Not too bad for a passphrase like “bolt vat frisky fob land hazy rigid,” which is entirely possible for most people to memorize. Compare that to “d07;oj7MgLz’%v,” a random password that contains slightly less entropy than the seven-word Diceware passphrase but is significantly more difficult to memorize.
In regards to passphrases, Ian Addison talks about getting younger students to combine two unrelated words that they can spell, while the eSafety team suggest providing multiple columns, where students choose one option from each. I wonder if a useful approach is to start with one word chosen from a simple list and progressively build up to something like four words taken from a more complicated list of words.
Supporting the process of reflection, passwords resource developed in conjunction with Code.org and Common Sense Media flips the various requirements into a series of statements. An approach could be used where each stage is defined by a different set of questions built up across time.
One of the other challenges to passwords being a ‘once-off’ activity is that such activities are often done to students, rather than with students. This often stems from the ramifications of poor passwords. For example, sometimes platforms have built-in feedback mechanisms that force users to enter a number, character and symbol. Also, based on logistics passwords are often managed for students using generators like Dinopass or Google Sheet tempaltes. Digital Technologies Hub’s answer to this is to go beyond a mere list of rules, suggesting that students create an artefact (i.e. a poster) explaining their understanding. Alternatively, sites like How Secure is My Password can be useful to support students for testing processes.
This all has me thinking about alternatives for logging in, such as the use of biometric information, patterns and images. I wonder what ‘passwords’ might look like for students in ten years time?
Share your thoughts on what you imagine to be the future of cyber attacks. Consider the types of information we store and share online today. What information will hackers try to get in the future? What approaches do you think they will use?
I think the future of hacking and cyber attacks is the linking of different datasets that we openly share online through data brokers to provide an insight and awareness of individuals that will open up new possibilities.
These companies often acquire the information through purchase, licensing, or other sharing agreements with third parties. Oracle, for example, “owns and works with” over 80 data brokers, according to a 2019 Financial Times report, aggregating information on everything from consumer shopping to internet behavior. However, many companies also scrape data that is publicly viewable on the internet and then aggregate it for sale or sharing. “People search” websites often fall into this latter category—compiling public records (property filings, court documents, voting registrations, etc.) on individuals and then letting anyone on the internet search for their information.
This impact is only amplified by the influx of connected devices and online accounts.
Unit 5 – Cyber Ethics
Find a resource (a website, video or storybook) for teaching a topic related to cyber ethics and share this with the community. Provide a brief explanation.
A useful post I have found in regards to cyber citizenship (and ethics) is Kathleen Morris’s Teaching Digital Citizenship: 10 Internet Safety Tips For Students (With Posters). Morris outlines her four layered approach to teaching digital citizenship. This focuses on integrating the various skills within the curriculum, providing real world stories to reflect upon, building up student toolkits and developing lines of communication. Associated with this, she also provides ten tips for students.Poste
Cyber Security & Awareness – Primary Years (CSER MOOC) by Aaron Davis is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.

Jon Keegan and Dara Kerr use Blacklight privacy inspector to demonstrate the data collected by trackers on abortion sites. It is another example of the way in which insight and awareness can be produced from the data trail we leave.
Canvs Editorial Dark Patterns are now illegal in India
—
I wonder who would actually follow-up with infringements of ‘dark patterns‘?
via Stephen Downes
Source: Dark Patterns Detective
A useful resource for walking through different dark patterns to add to my work as a part of the CSER MOOC.